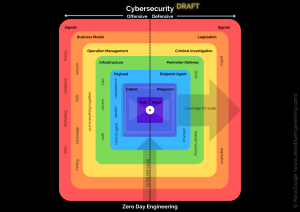
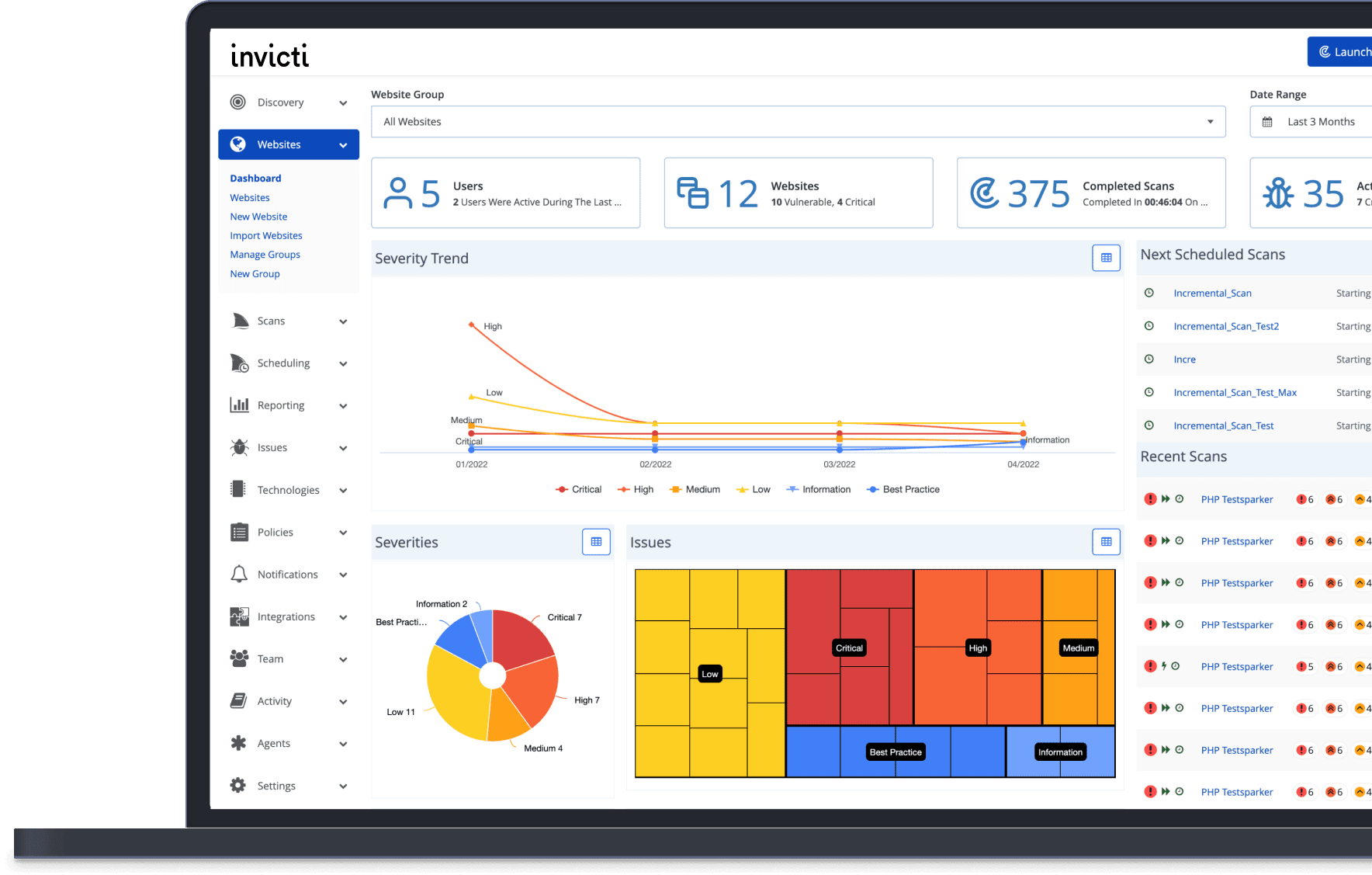
SentinelOne University offers cybersecurity training programs, including a comprehensive Threat Hunting course. Whether you’re a system administrator seeking to enhance your skills or a seasoned threat hunter looking to expand your toolkit, this course has actionable and insightful content for every role and experience level.
Here are the key highlights of the SentinelOne University Threat Hunting course:
-
- The course focuses on repeatable and documentable cyber threat hunting methodologies.
- Participants will learn about various tools that enhance the effectiveness of threat hunting.
Whether you’re diving into threat hunting for the first time or refining your expertise, SentinelOne University provides the resources you need to stay ahead in the ever-evolving cybersecurity landscape. 🛡️🔍