
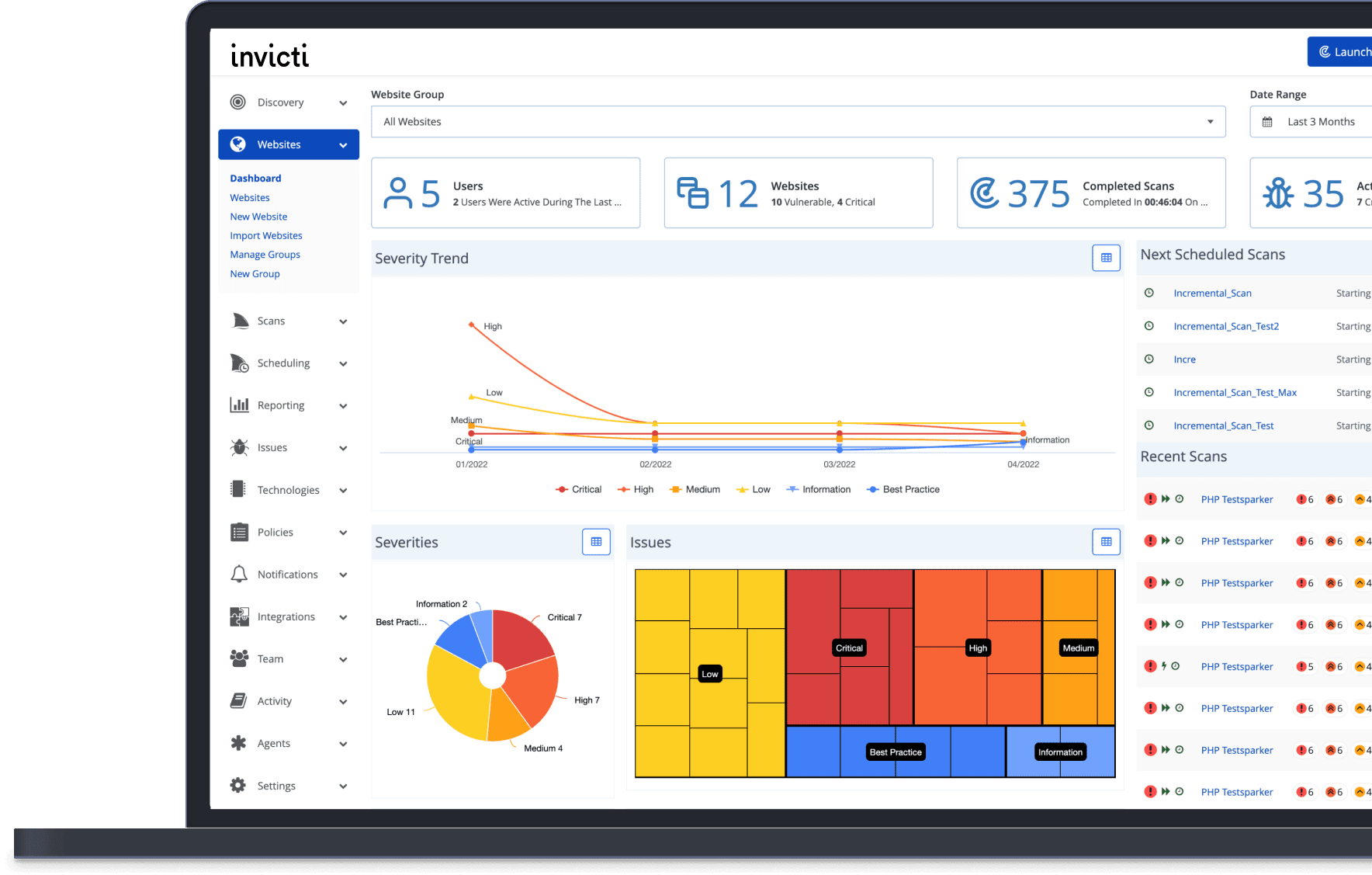
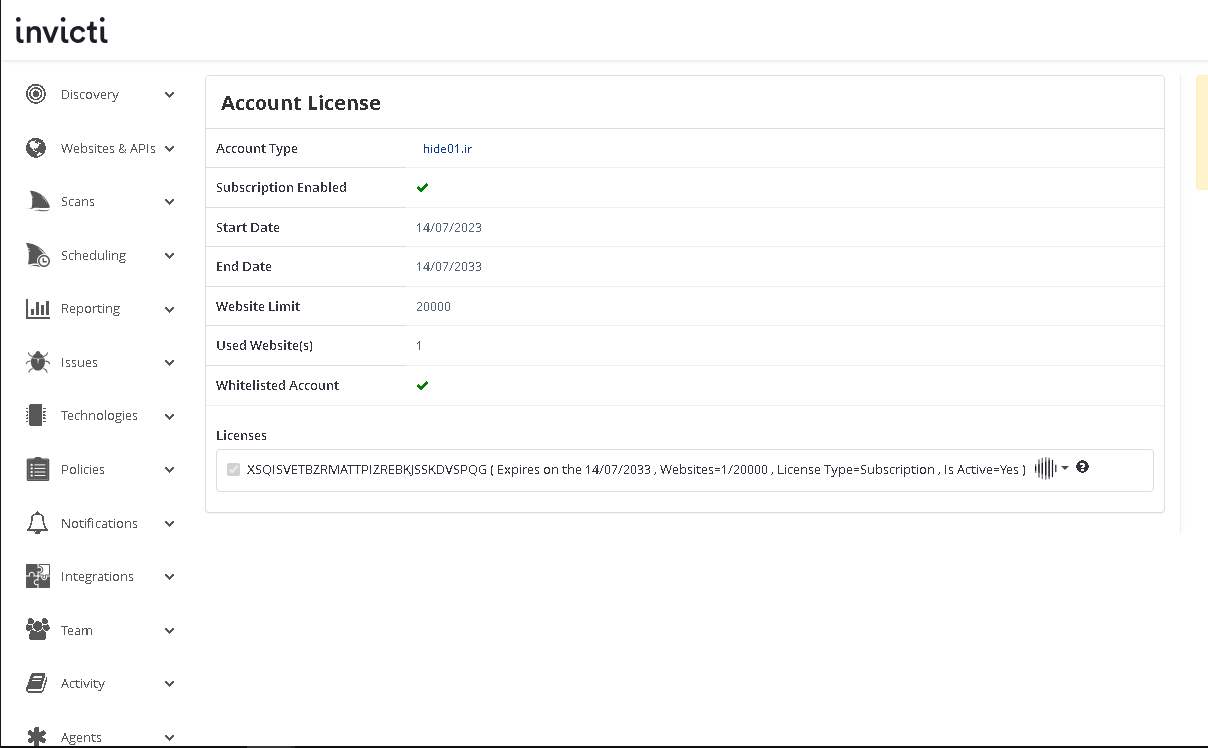
Invicti – Web Application Security For Enterprise




Tenable Nessus is a powerful vulnerability scanner that helps you identify and fix security issues in your network, web applications, cloud infrastructure, and more. With Nessus, you can:

LEG523 is a specialized course designed to provide participants with a comprehensive understanding of the legal frameworks and regulatory environments that govern cybersecurity and data privacy. This course is ideal for legal professionals, compliance officers, and cybersecurity practitioners who need to navigate the complex intersection of technology and law.

MGT514 is a professional training course designed to help cybersecurity and IT leaders develop the skills and strategies necessary for managing and leading security programs. The course focuses on aligning security initiatives with business objectives, building a strong governance framework, and driving organizational resilience against modern threats.

DevOps is taking the world by storm, but the often overlooked part is that keeping applications secure is increasingly important. So how do you keep your entire development chain secure and within compliance? This path answers that question by showing you the fundamentals of DevSecOps and keeping your CI/CD pipelines safe while incorporating security best practices into your DevOps lifecycle.

In this course, you will learn to reverse engineer. That will allow you to protect intellectual property, find vulnerabilities, and pull apart malware. Join me in making the world a little safer. In the prior courses we learned there are 4 main techniques to secure code: design review, static analysis, manual audit, and dynamic (fuzz) testing. But, once the code is fielded, hackers will begin researching exploits against it. In this course, learn how and why compiled binaries are examined and scoured for weaknesses, and why reversing is also a required malware analysis skill and is sometimes needed for low-level developers working with undocumented APIs. After watching this course you’ll be familiar all of the above and with the popular IDA pro tool and how to use it. Download the IDA pro demo to complete the labs.