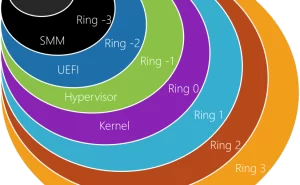
Here is a brief description of the Windows Kernel Programming Class Recordings course offered by Pavel Yosifovich : The course is designed to provide an in-depth understanding of Windows kernel programming. It covers topics such as Windows Internals Overview, Device Driver Basics, Kernel Mechanisms, and Miscellaneous Techniques. The course is divided into 9 modules and is approximately 32 hours long. The course materials include PDFs, labs, and solutions to the labs. The course recordings are available for purchase at a cost of 490 USD. If you’re interested in purchasing the course, you can send an email to zodiacon@live.com with the title “Kernel Programming class recordings” 1. Once you’ve paid, you’ll receive a link to the course recordings along with the course materials. You’ll also receive a 10% discount for the Advanced Windows Kernel Programming class in April, be added to a discord server that will host all the Alumni from my public classes, and have a live session with Pavel sometime in early April where you can ask questions about the class .
Syllabus
- Module 0: Introduction
- Module 1: Windows Internals Overview
- Module 2: The I/O System
- Module 3: Device Driver Basics
- Module 4: The I/O Request Packet
- Module 5: Kernel Mechanisms
- Module 6: Process and Thread Monitoring
- Module 7: Object and Registry Notifications
- Module 8: File System Mini-Filters Fundamentals
- Module 9: Miscellaneous Techniques
ScorpioSoftware: Windows Kernel Programming