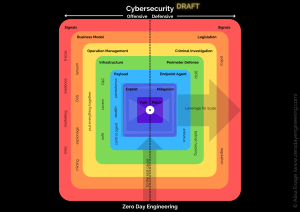
This course covers key aspects of cybersecurity, including understanding threats, vulnerabilities, and the necessary countermeasures. It may also delve into specialized areas such as zero-day vulnerability research.

This course covers key aspects of cybersecurity, including understanding threats, vulnerabilities, and the necessary countermeasures. It may also delve into specialized areas such as zero-day vulnerability research.

This 4-day course cuts through the mystery of Cloud Services (including AWS, Azure, and G-Cloud) to uncover the vulnerabilities that lie beneath. We will cover a number of popular services and delve into both what makes them different, and what makes them the same, as compared to hacking and securing traditional network infrastructure. Whether you are an Architect, Developer, Pentester, Security or DevOps Engineer, or anyone with a need to understand and manage vulnerabilities in a Cloud environment, understanding relevant hacking techniques, and knowing how to protect yourself from them is critical. This course covers both the theory as well as a number of modern techniques that may be used to compromise various Cloud services and infrastructure. Prior pentest/security experience is not a strict requirement, however, some knowledge of Cloud Services and familiarity with common Unix command-line syntax will be beneficial.

This is a hand-on practical concentrated course on securing and attacking web and cloud APIs. APIs are everywhere nowadays: In web apps, embedded systems, enterprise apps, cloud environments and even IoT, and it is becoming increasingly necessary to learn how to defend, secure and attack API implementation and infrastructure. This training aims to engage you in creating secure modern APIs, while showing you both new and old attack vectors.
Defending and attacking Web APIs (REST, GraphQL..etc)
Attacking and securing AWS APIs and infrastructure.
Launching and mitigating modern Injection attacks (SSTI, RCE, SQLi, NoSQLi, Deserialization & object injection)
Deploying practical cryptography.
Securing passwords and secrets in APIs.
API authentication and authorization.
Targeting and defending API architectures (Serverless, web services, web APIs)
Securing development environments.

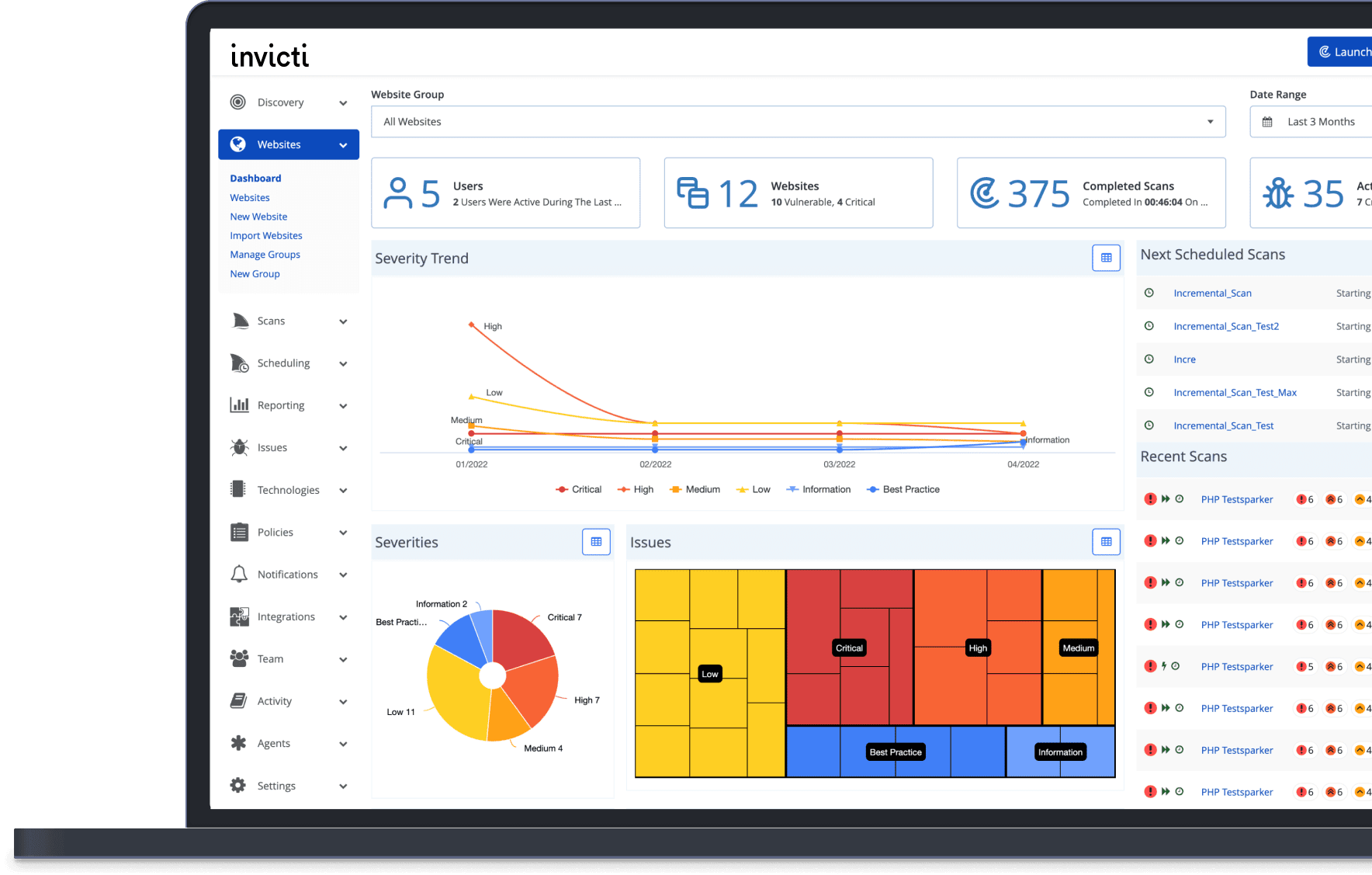

Tenable Nessus is a powerful vulnerability scanner that helps you identify and fix security issues in your network, web applications, cloud infrastructure, and more. With Nessus, you can:

This course covers the law of fraud, crime, policy, contracts, liability, IT security and active
defense—all with a focus on electronically stored and transmitted records. It also teaches
investigators how to prepare credible, defensible reports, whether for cyber crimes, forensics,
incident response, human resource issues or other investigations.
Each successive day of this five-day course builds upon lessons from the earlier days in order to
comprehensively strengthen your ability to help your enterprise (public or private sector) cope
with illegal hackers, botnets, malware, phishing, unruly vendors, data leakage, industrial spies,
rogue or uncooperative employees, or bad publicity connected with IT security.
Recent updates to the course address hot topics such as legal tips on confiscating and
interrogating mobile devices, the retention of business records connected with cloud computing
and social networks like Facebook and Twitter, and analysis and response to the risks and
opportunities surrounding open-source intelligence gathering
SECTION 1: Fundamentals of Data Security Law and Policy
SECTION 2: E-Records, E-Discovery and Business Law
SECTION 3: Contracting for Data Security and Other Technology
SECTION 4: The Law of Data Compliance: How to Conduct Investigations
SECTION 5: Applying Law to Emerging Dangers: Cyber Defense