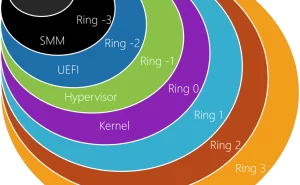
The Windows OS exposes many advanced services to system programmers through the Windows API, and to device driver writers through the Kernel API. The .NET framework wraps these services and runs on top of the Windows API and the Kernel. Good knowledge of what’s going on under the hood of the OS, which services are available and how to best utilize them helps in building better and more efficient software for Windows. Those working in the Cyber security space can greatly benefit from the course as it looks at all major Windows mechanisms. Lab exercises are used to reinforce the theoretical material.
Syllabus
System Architecture
Processes & Jobs
Threads
Memory Management
I/O System
Security






