
Invicti – Web Application Security For Enterprise
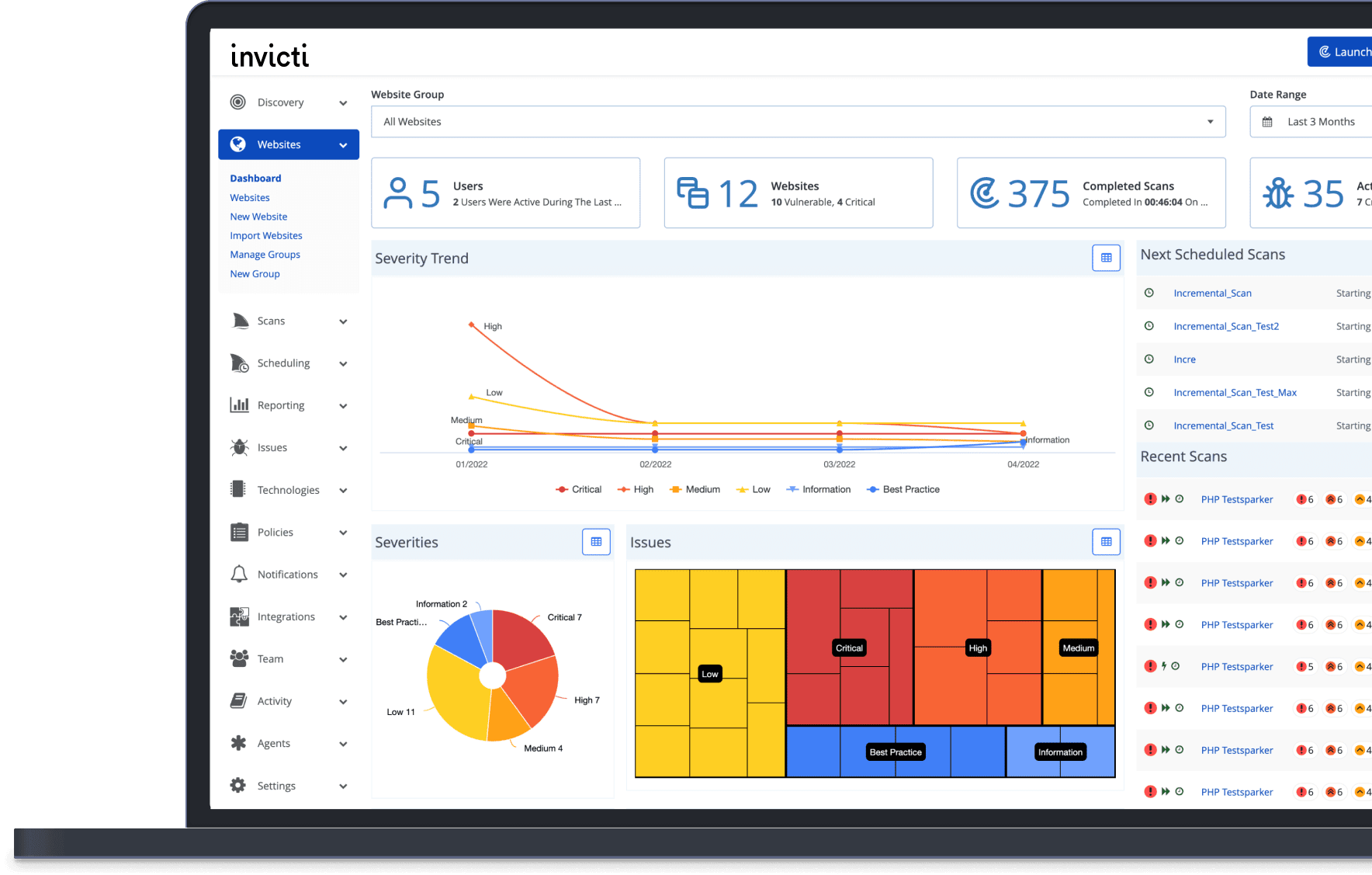




Acunetix is a web application security scanner that helps you find and fix vulnerabilities in your web applications, web services, and APIs. It can scan any website or web application that uses HTTP or HTTPS protocol and supports various frameworks, languages, and technologies. Acunetix can detect over 7,000 types of vulnerabilities, including OWASP Top 10, SQL injection, XSS, misconfigurations, exposed databases, and more. It also provides vulnerability assessment and management features, such as severity ratings, remediation guidance, false positive reduction, and integration with development tools. Acunetix is available as an on-premise or cloud solution and can be used by businesses of all sizes to automate web application security testing and ensure long-term protection.

Tenable Nessus is a powerful vulnerability scanner that helps you identify and fix security issues in your network, web applications, cloud infrastructure, and more. With Nessus, you can:

This path will cover the essential tasks of web application pen testing, walking through each phase of the methodology as if you are shadowing a live application pen test. The scenario will cover testing through an application, discovering and exploiting vulnerabilities found. In addition, there are many vulnerabilities that a web app pen tester should be able to identify and test for. Don’t miss the specialized courses covering a deep-dive into each of these types of vulnerabilities.
Web App Pen Testing: Reconnaissance
Specialized Testing: Sessions and Tokens
Web App Pen Testing: MappingSpecialized Testing: XSS
Specialized Testing: SQL InjectionSpecialized Testing: CSRF
Specialized Testing: DeserializationSpecialized Testing: API Testing
Specialized Testing: Command Injection
Pluralsight – Web App Pen Testing

This series provides the foundational knowledge needed to ethically and effectively discover and exploit vulnerabilities in systems by assuming both the mindset and toolset of an attacker. Through learning how systems are attacked you will gain an understanding of how best to protect systems and improve your organization’s security
Understanding Ethical Hacking
Reconnaissance/Footprinting
Scanning Networks
Enumeration
Vulnerability Analysis
System Hacking
Malware Threats
Sniffing
Social Engineering
Denial of Service
Session Hijacking
Evading IDS, Firewalls, and Honeypots
Hacking Web Servers
Hacking Web Applications
SQL Injection
Hacking Wireless Networks
Hacking Mobile Platforms
Hacking the Internet of Things (IoT)
Cloud Computing
Cryptography
Penetration Testing

You’ve heard this story before. Bad actor walks into a network and pillages the place in swift action. CIO asks: “Where did we go wrong?” SysAdmin replies “our password, remote access, workstation restriction, and lack of application safelisting policies. Oh, and our SIEM didn’t notify us. We just weren’t ready for that attack.”
In a significant change from the original course, students will be introduced to Microsoft Azure and Sentinel. Each student will be responsible for deploying a cloud lab that includes an Active Directory domain, a C2 server, and integration with AZ Sentinel’s detection platform. All of this will be taught through a proven framework for purple team operations that results in better business outcomes.
Each student will then pollute the AD domain with garbage using BadBlood and wreak havoc on the environment through an updated iteration of the following labs: